Fig A
Basically, a mail rule decides how to process incoming messages as they are received. You can create rules to divert messages from a specific person or group to a designated folder. For example, you can customize rules to block spam e-mail or to intercept messages with questionable content.
Mail rules work like this: Whenever a message is received, the Inbox evaluates the fields in the message against registered mail rules. When a message meets a defined condition, Lotus Notes takes the specified action with that message.
When creating a new rule, users must define two parts of the rule: the condition and the action. The condition defines the rule criteria, and the action defines what the system does to the message if the condition is met.
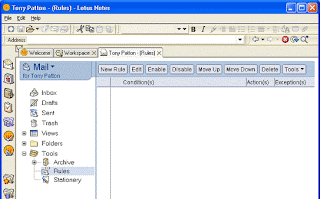
Available rules
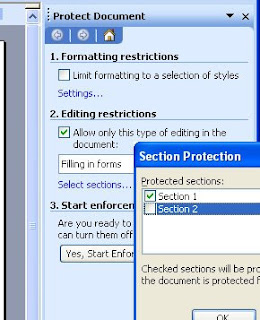
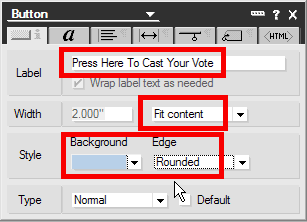
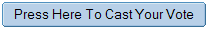
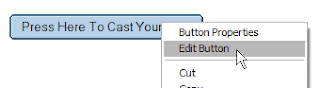
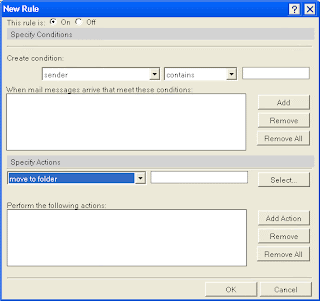
To create a rule, click the Create Rule button shown in Figure A to get to the dialog box shown in Figure B, which allows the user to set the various characteristics of a rule. To set the characteristics, the user chooses a property of the e-mail, and adds the condition under which the e-mail should be diverted.
Fig B
Rules may be created using the following mail message properties:
* Sender
* Subject Line
* Body
* Importance
* Delivery Priority
* To
* CC
* BCC
* To Or CC
* Body Or Subject Line
* Internet Domain
* Message Size (In Bytes)
* All Documents
Fig C
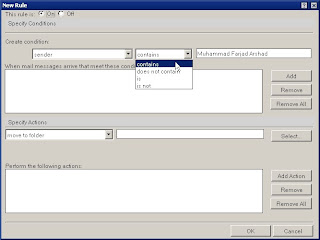
Now Add this rule
Fig D
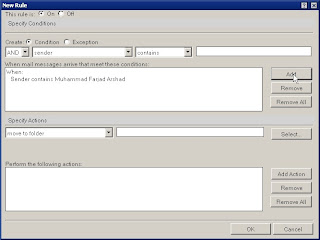
The last option (All documents) is used to define a rule for every message received. The other options allow specific aspects of the message to be used in the rule. Once the property is selected, the next step is adding the condition. Figure C shows the options, which include:
* Contains: The rule property must contain the specific text
* Does Not Contain: The rule property does not contain the specific text
* Is: The rule property equals the specific text
* Is Not: The rule property does not equal the specific text
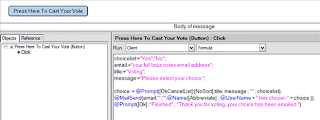
Next, users should add the specific criteria in the text box. For example, Figure C shows the creation of a rule that processes all messages that have Muhammad Farjad Arshad in the sender line. Then, the criteria is added to the rule by selecting the Add button. Existing criteria may be removed with the Remove button, or the Remove All button may be used to delete all criteria.
Adding the action
At this point, the rule criteria have been established. Now users must specify where the messages that meet the criteria should go. The Specify Actions section at the bottom of the dialog box, shown in Figure D, allows a user to indicate what should happen to messages. You have the following options for Actions:
* Move To Folder: The message is moved to the specified folder; message removed from Inbox
* Copy To Folder: The message is copied to the specified folder; message remains in Inbox
* Send Copy To: A copy of the message is sent to the specified user(s); can send full message or only the headers
* Set Expire Date: Message expiration date is set (number of days, weeks, months, or years)
* Change Importance To: Message importance is set (high, medium, low)
* Delete: The message is deleted from the Inbox
For this Press "Select" button and press "Create New Folder"
FIG E
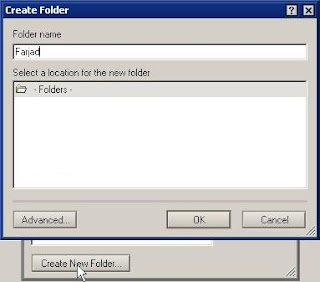
After this Press "OK" then Press "OK"
The Copy To Folder and Move To Folder options allow the user to choose a destination folder. Users should click the Select button and they will be presented with the Folders box shown in Figure E where they can choose the destination folder. Multiple folder options can be created; they can be added with the Add button (shown in Figure). Again, the Remove and Remove All buttons are used to delete existing options.
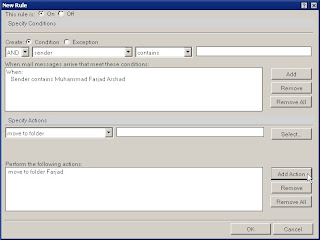
Now press Ok