This blog is for technology oriented people who wants to know new rapidly changing technologies. http://feeds.feedburner.com/blogspot/farjad
Saturday, December 27, 2008
Effective search from Gooogle
AND [&] (ampersand) Slackware AND Linux Shows pages containing both arguments, *OBS* this is the default operator, no need to include
OR [|] (pipe) Laptop OR Desktop Shows pages containing either argument
- (minus) Hamburger -McDonalds Shows pages containing the word "Hamburger", but only if they don't mention "McDonalds"
+ (plus) +coke Contrary to the "includes" belief, this limits the results to the given form only, no pluralis or other tenses
~ (tilde) ~Hacker Results include everything deemed similar to "Hacker"
* (asterisk) Fish * Chips The wildcard (*) is replaced by one or more words/characters (and, n, 'n, &)
define: define:Nocturnal A personal favorite, looks up the meaning of the word
site: Phreaking site:phrack.org Limits the search to a specific site
#...# zeroday 2007...2008 Search results include a value within the given range
info: info:www.hacktivismo.com Shows information about the site
related: related:www.google.com Shows pages similar/related to argument
link: link:www.darkmindz.com Shows sites linking to the argument
filetype: phrack filetype:pdf Results are limited to given filetype
([?]) Cyber (China & America) Nestling combines several terms in the same query
[?A] in [?B] 1 dollar in yen Converts argument A to argument B
daterange: daterange:2452122-2452234 Results are within the specified daterange. Dates are calculated by the Julian calendar
movie: movie:Hackers Movie reviews, can also find movie theaters running the movie in U.S cities
music: music:"Weird Al" Hits relate to music
stock: stock: goog Returns stock information (NYSE, NASDAQ, AMEX)
time: time: Stockholm Shows the current time in requested city
safesearch: safesearch: teen Excludes pornography
allinanchor: allinanchor: Best webcomic ever" Results are called argument by others
inanchor: foo bar inanchor:jargon As above, but not for all. The corresponding below all bear the same meaning
allintext: allintext:8-bit music Argument exists in text
intext:
allintitle: allintitle: Portfolio Argument exists in title
intitle:
allinurl: allinurl:albino sheep Argument exists in URL
inurl:
Advanced
GET-variable breakdown
http://www.google.com/search?
as_q=test (query string)
&hl=en (language)
&num=10 (number of results [ 10,20,30,50,100 ])
&btnG=Google+Search
&as_epq= (complete phrase)
&as_oq= (at least one)
&as_eq= (excluding)
&lr= (language results. [ lang_countrycode ])
&as_ft=i (filetype include or exclude. [i,e])
&as_filetype= (filetype extension)
&as_qdr=all (date [ all,M3,m6,y ])
&as_nlo= (number range, low)
&as_nhi= (number range, high)
&as_occt=any (terms occur [ any,title,body,url,links ])
&as_dt=i (restrict by domain [ i,e ])
&as_sitesearch= (restrict by [ site ])
&as_rights= (usage rights [ cc_publicdomain, cc_attribute, cc_sharealike, cc_noncommercial, cc_nonderived ]
&safe=images (safesearch [ safe=on,images=off ])
&as_rq= (similar pages)
&as_lq= (pages that link)
&as_qdr= (get only recently updated pages d[ i ] | w[ i ] | y[ i ])
&gl=us (country)
Googledorks
So, Google gives us all those handy tools for filtering away what we don't want to see, how can we use this to help securing our own systems?
Well, for example, we could use the neat Google Hacking Database, a project where people has submitted a huge collection of queries yielding results that the unskilled webmaster (the Googledork) wishes weren't there. Everything from vulnerable login-forms to passwords surfaces with some cleverly engineered queries.
Goolag
Goolag is a vulnerability scanner (and a politically involved protest..) made by the famous Cult of the Dead Cow. It builds on the above mentioned GHDB, scanning for vulnerabilities in the database. At the moment there is only a Windows-version of the program. The Goolag project is also a campaign against Google's (and a few other big players') choise to comply with the Chinese censorship policy.
Useful Queries
-inurl:htm -inurl:html intitle:"index of" "Last modified" mp3 mp3-file indexes, add desired artist
site:rapidshare.de -filetype:zip OR rar daterange:2453402-2453412 zip files on rapidshare uploaded on specified date
http://www.google.com/search?q=your+query+here&as_qdr=d1 Query results updated within one day
Places where viruses and trojans hide in Windows
Notice that I did not say that Windows "runs" every program that is represented in the Start Up folder. I said it "opens every item." There's an important difference.
Programs represented in the Start Up folder will run, of course. But you can have shortcuts in the Start Up folder that represent documents, not programs.
For example, if you put a Microsoft Word document in the Start Up folder, Word will run and automatically open that document at bootup; if you put a WAV file there, your audio software will play the music at bootup, and if you put a Web-page Favourites there, Internet Explorer (or your own choice of a browser) will run and open that Web page for you when the computer starts up. (The examples cited here could just as easily be shortcuts to a WAV file or a Word document, and so on.)
2. REGISTRY. Windows executes all instructions in the "Run" section of the Windows Registry. Items in the "Run" section (and in other parts of the Registry listed below) can be programs or files that programs open (documents), as explained in No. 1 above.
3. REGISTRY. Windows executes all instructions in the "RunServices" section of the Registry.
4. REGISTRY. Windows executes all instructions in the "RunOnce" part of the Registry.
5. REGISTRY. Windows executes instructions in the "RunServicesOnce" section of the Registry. (Windows uses the two "RunOnce" sections to run programs a single time only, usually on the next bootup after a program installation.)
7. REGISTRY. Windows executes instructions in the HKEY_CLASSES_ROOT\exefile\shell\open\command "%1" %* section of the Registry. Any command imbedded here will open when any exe file is executed.
Other possibles:
[HKEY_CLASSES_ROOT\exefile\shell\open\command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\comfile\shell\open\command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\batfile\shell\open\command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\htafile\Shell\Open\Command] ="\"%1\" %*"
[HKEY_CLASSES_ROOT\piffile\shell\open\command] ="\"%1\" %*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\batfile\shell\open\command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\comfile\shell\open\command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\exefile\shell\open\command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\htafile\Shell\Open\Command] ="\"%1\"
%*"
[HKEY_LOCAL_MACHINE\Software\CLASSES\piffile\shell\open\command] ="\"%1\"
%*"
If keys don't have the "\"%1\" %*" value as shown, and are changed to something like "\"somefilename.exe %1\" %*" than they are automatically invoking the specified file.
8. BATCH FILE. Windows executes all instructions in the Winstart batch file, located in the Windows folder. (This file is unknown to nearly all Windows users and most Windows experts, and might not exist on your system. You can easily create it, however. Note that some versions of Windows call the Windows folder the "WinNT" folder.) The full filename is WINSTART.BAT.
9. INITIALIZATION FILE. Windows executes instructions in the "RUN=" line in the WIN.INI file, located in the Windows (or WinNT) folder.
10. INITIALIZATION FILE. Windows executes instructions in the "LOAD=" line in the WIN.INI file, located in the Windows (or WinNT) folder.
It also runs things in shell= in System.ini or c:\windows\system.ini:
[boot]
shell=explorer.exe C:\windows\filename
The file name following explorer.exe will start whenever Windows starts.
As with Win.ini, file names might be preceeded by considerable space on such a line, to reduce the chance that they will be seen. Normally, the full path of the file will be included in this entry. If not, check the \Windows directory
11. RELAUNCHING. Windows reruns programs that were running when Windows shut down. Windows cannot do this with most non-Microsoft programs, but it will do it easily with Internet Explorer and with Windows Explorer, the file-and-folder manager built into Windows. If you have Internet Explorer open when you shut Windows down, Windows will reopen IE with the same page open when you boot up again. (If this does not happen on your Windows PC, someone has turned that feature off. Use Tweak UI, the free Microsoft Windows user interface manager, to reactivate "Remember Explorer settings," or whatever it is called in your version of Windows.)
12. TASK SCHEDULER. Windows executes autorun instructions in the Windows Task Scheduler (or any other scheduler that supplements or replaces the Task Scheduler). The Task Scheduler is an official part of all Windows versions except the first version of Windows 95, but is included in Windows 95 if the Microsoft Plus Pack was installed.
13. SECONDARY INSTRUCTIONS. Programs that Windows launches at startup are free to launch separate programs on their own. Technically, these are not programs that Windows launches, but they are often indistinguishable from ordinary auto-running programs if they are launched right after their "parent" programs run.
14. C:\EXPLORER.EXE METHOD.
C:\Explorer.exe
Windows loads explorer.exe (typically located in the Windows directory)during the boot process. However, if c:\explorer.exe exists, it will be executed instead of the Windows explorer.exe. If c:\explorer.exe is corrupt, the user will effectively be locked out of their system after they reboot.
If c:\explorer.exe is a trojan, it will be executed. Unlike all other autostart methods, there is no need for any file or registry changes - the file just simply has to be named c:\explorer.exe
15. ADDITIONAL METHODS.
Additional autostart methods. The first two are used by Trojan SubSeven 2.2.
HKEY_LOCAL_MACHINE\Software\Microsoft\Active Setup\Installed Components
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\Currentversion\explorer\Usershell folders
Icq Inet
[HKEY_CURRENT_USER\Software\Mirabilis\ICQ\Agent\Apps\test]
"Path"="test.exe"
"Startup"="c:\\test"
"Parameters"=""
"Enable"="Yes"
[HKEY_CURRENT_USER\Software\Mirabilis\ICQ\Agent\Apps\]
This key specifies that all applications will be executed if ICQNET Detects an Internet Connection.
[HKEY_LOCAL_MACHINE\Software\CLASSES\ShellScrap] ="Scrap object"
"NeverShowExt"=""
This key changes your file's specified extension.
Tuesday, December 9, 2008
Tuesday, November 18, 2008
Autometically sort the program Menu Alphabetically
2. Go to:
HKEY_Current_User\Software\Microsoft\
Windows\CurrentVersion\Explorer\MenuOrder
3. With MenuOrder highlighted, open the Edit menu (on the Tool bar), select permissions.
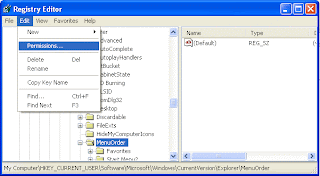
4.This will open the “Permissions for MenuOrder” dialog box. Click the Advanced button
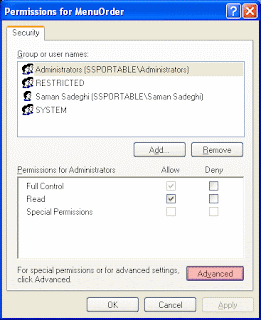
5.This will open the “Advanced Security Settings for MenuOrder” dialog box. Clear the “Inherit From Parent . . .” check box.
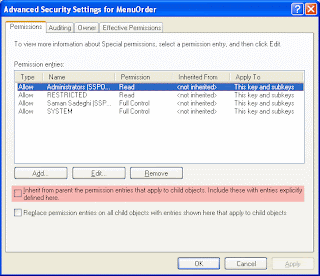
6.In the security dialog box that appears, click Copy:
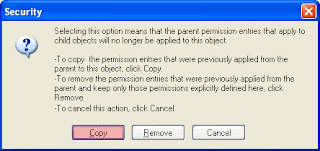
7.Click OK to return the “Permissions for MenuOrder“dialog box, and then clear the “Full Control Access” entry for your own account and for any security groups that you’re a member of, leaving the “Read Access Control” entry in place.
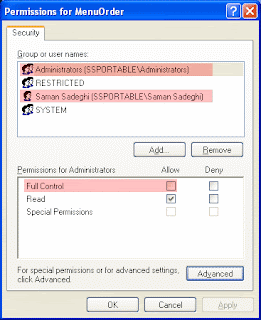
8.Click OK and you’re done!
Autometically kill program at shutdown
1. Hit the Windows Key+R, type regedit into the run dialog and hit OK.
2. Now that you’re in the the Registry, navigate to this key:
HKEY_CURRENT_USER\Control Panel\Desktop
The AutoEndTasks Key In The System Registry
3. Double click the AutoEndTasks key (in the right pane) and change the Value Data to 1
4. Close the Registry and restart your machine to enable the change!
Now, when you shut down this computer, all programs will be killed and the computer shouldn’t be delayed!
Thursday, November 13, 2008
The Golden Rule of Deleting a 'Cannot Delete File error' file in WinXp
2 - Select the process called "explorer.exe" and right click and end this process.
3 - You will get a blank desktop with only the windows task manager running.
4 - Click top left menu; File > New task (Run...)
5 - A window opens for you to select the new task, click
6 - A browse window opens. Make sure that you change the selection: "Files of types" from 'Programs' to 'All files'
7 - Then Browse to the folder and file that you want to delete. Select it and press delete. You should be able to delete it now.(unless it is a persistent primary windows system file)
8 - once deleted, go browse to c:windowsexplorer and open it.
You should be returned to where you were in the first place. Happy deleting.
Increase Harddrive read/write speed
In any case, it won't harm your system, so try it yourself and let me know what you find!
Steps:
1. Run SYSEDIT.EXE from the start & then Run command.
2. Expand the system.ini file window.
3. Scroll down almost to the end of the file untill you find a line called [386enh].
4. Press Enter to make one blank line, and in that line type
5. Irq14=4096 (note: This line IS CASE SENSITIVE)
6. Click on the File menu, then choose Save.
7. Close SYSEDIT and reboot your computer.
8. Restart windows!
The speed improvement will be noticed just after the system reboots, any system info. software can be used to check the improvement.
Make Mozilla Firefox 10 time faster
1. Type "about:config" into the address bar and hit enter. Scroll down and look for the following entries:
2. Alter the entries as follows:
Set "network.http.pipelining" to "true"
Set "network.http.proxy.pipelining" to "true"
set "network.http.pipelining.maxrequests" to some number like 30. This means it will make 30 requests at once.
3. Lastly right-click anywhere and select New-> Integer. Name it "nglayout.initialpaint.delay" and set its value to "0". This value is the amount of time the browser waits before it acts on information it recieves.
NOTE:this trick only works for broadband users not for dialup
Set default folder for attachment in Outlook 2003
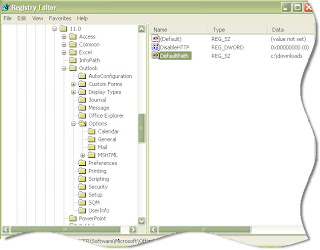
Do not panic I am here to provide you the solution. The default download location can be changed by opening regedit and drilling down to this registry key:
HKEY_CURRENT USER\Software\Microsoft\Office\11.0\Outlook\Options
Create a new string value under this key (If it does not already exist) named DefaultPath, and set the value to the absolute path you would like to use as your default location.
In my case I wanted to change it to c:\downloads\ Here is what it looks like in the registry:
so now when I go to save an attachment, I don't need to fish around for the downloads folder - it automatically defaults right to it:
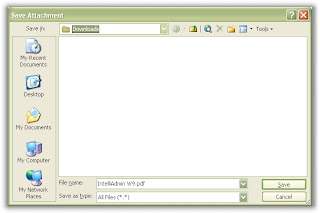
Here you are.
Set Multiple home pages for IE 7 from the command line
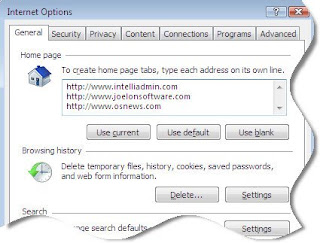
I added some websites, and then I dug into the registry to see what was changed. Here is a snapshot:
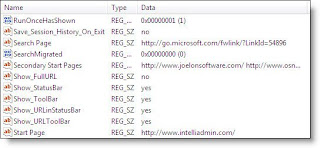
That there are actually two parts to the home page setting. They are both under HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main
The first website to be displayed is stored under the string value named:
Start Page
The rest of the websites displayed are stored in a string array value named:
Secondary Start Pages
The first string is very easy to script and change.
The second is not as simple. This is because it is an array of strings separated by NULL characters, and terminated with two NULL characters.
There are a few ways to do this. One way would be to update one machine with all of your desired settings...and create an exported reg key. You could then use regedit in silent mode to import the settings on other machines.
This has its downfalls - if not done right you could accidentally pull in other values you don't want thrown around to every machine.
Another way would be to use VB Script. I wanted something cleaner, and an excuse to start using our new internal API for writing cross-compilable software (64 and 32 bit). I came up with this little command line program named IESetHomeTabs.exe
Here is how you call it from the command line:
C:>IESetHomeTabs.exe "[URL1]" "[URL2]" "[URL3]"
So if I wanted http://www.intelliadmin.com, http://www.slashdot.org, and http://www.technet.com as my 3 tabs I could call it like this:
C:>IESetHomeTabs.exe "http://www.intelliadmin.com" "http://www.slashdot.org" "http://www.technet.com"
Shutdown your computer in one click
It is really simple, and this will work under Windows XP, and 2003 - not sure if it will work under Vista, but I would imagine the UAC prompt would ruin the whole experience.
Open notepad and put in the following text:
shutdown.exe -s -t 00
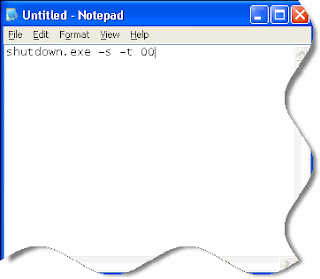
Save it on the desktop as "Shutdown.bat"
Now if you double click on the icon "Shutdown" your system will shutdown immediately with no questions asked.
How to remove a misspelled word from MSWord 2007 Dictionary
However, once you add a word to a dictionary, you can also delete it at any time using the steps listed below.
To delete a word from a dictionary in Word 2007:
• Click the Microsoft Office Button and click Word Options.
• Click Proofing.
• Click Custom Dictionaries.
• Select the dictionary list you want to modify and click Edit Word List.
• Select the appropriate word in the Dictionary box and click Delete.
• Repeat this step for each additional word you want to remove from the dictionary.
Wednesday, November 5, 2008
23 Hidden XP Applications
1) Character Map = charmap.exe (very useful for finding unusual characters)
2) Disk Cleanup = cleanmgr.exe
3) Clipboard Viewer = clipbrd.exe (views contents of Windows clipboard)
4) Dr Watson = drwtsn32.exe (Troubleshooting tool)
5) DirectX diagnosis = dxdiag.exe (Diagnose & test DirectX, video & sound cards)
6) Private character editor = eudcedit.exe (allows creation or modification of characters)
7) IExpress Wizard = iexpress.exe (Create self-extracting / self-installing package)
8 Mcft Synchronization Manager = mobsync.exe (appears to allow synchronization of files on the network for when working offline. Apparently undocumented).
9) Windows Media Player 5.1 = mplay32.exe (Retro version of Media Player, very basic).
10) ODBC Data Source Administrator = odbcad32.exe (something to do with databases)
11) Object Packager = packager.exe (to do with packaging objects for insertion in files, appears to have comprehensive help files).
12) System Monitor = perfmon.exe (very useful, highly configurable tool, tells you everything you ever wanted to know about any aspect of PC performance, for uber-geeks only )
13) Program Manager = progman.exe (Legacy Windows 3.x desktop shell).
14) Remote Access phone book = rasphone.exe (documentation is virtually non-existant).
15) Registry Editor = regedt32.exe [also regedit.exe] (for hacking the Windows Registry).
16) Network shared folder wizard = shrpubw.exe (creates shared folders on network).
17) File siganture verification tool = sigverif.exe
18 Volume Contro = sndvol32.exe (I've included this for those people that lose it from the System Notification area).
19) System Configuration Editor = sysedit.exe (modify System.ini & Win.ini just like in Win98! ).
20) Syskey = syskey.exe (Secures XP Account database - use with care, it's virtually undocumented but it appears to encrypt all passwords, I'm not sure of the full implications).
21) Mcft Telnet Client = telnet.exe
22) Driver Verifier Manager = verifier.exe (seems to be a utility for monitoring the actions of drivers, might be useful for people having driver problems. Undocumented).
23) Windows for Workgroups Chat = winchat.exe (appears to be an old NT utility to allow chat sessions over a LAN, help files available).
Note:- Some of them might not run in Windows XP Home edition
Tuesday, November 4, 2008
Remove The Text From An Icon

Are you very good with figuring out what program corresponds to what icon? If so, you may be interested in this guide. This guide with show you how to remove the titles of the various icons. You may be thinking that it is very easy to remove the titles. Probably your first thought would be to rename the icon and make a blank name. Well, that doesn’t work, if you don’t believe me try it out for yourself and see….
What happens when you try to rename the icon to a blank name? It simply reverts back to the previous name.![]()
For this trick to work, we need to make sure that File and Folder Settings has the Show File Extensions for known File Types Enabled. This is the default setting in XP, so if you have not made any changes it should be set properly. If you are not sure, then check. Here is how …
Click Start, then My Computer. Click on Tools then Folder Options.
On the View tab check mark Hide Extensions For Known File Types then Click Apply Ok, now that we have that set...Here is the trick to removing the icon title and having a Blank Text untitled icon First, right click on the icon that you want to remove it’s title, then go to Rename Now, what you need to do, is hold the ALT button down. With the ALT button held down, and using the keypad type 255 then release the ALT button and hit enter, and voila you now have a untitled icon. This trick will work only for icon, if you are creating multiple Blank Text icons then you will need to name them like this: AFTER:![]()
The reason we need to do this is because part of Windows XP rules state that you cannot have a file/folder/shortcut with the same name in the same folder. To get around this restriction, we simply name the first icon with 1 blank space, the second icon with 2 blank spaces, the third with 3 blank spaces and so on.
FUN, TECH. HOW TO HIDE A FILE IN A IMAGE ! ! !
-The image will hereby be referred to in all examples as fluffy.jpg
-The file will hereby be referred to in all examples as New Text Document.txt
2. Add the file/files you will be injecting into the image into a WinRar .rar or .zip. From here on this will be referred to as (secret.rar)
3. Open command prompt by going to Start > Run > cmd
4. In Command Prompt, navigate to the folder where your two files are by typing
cd location [ex: cd C:\New Folder]
5. Type [copy /b fluffy.jpg + secret.rar fluffy.jpg] (remove the brackets)
Congrats, as far as anyone viewing is concerned, this file looks like a JPEG, acts like a JPEG, and is a JPEG, yet it now contains your file.
In order to view/extract your file, there are two options that you can take
a) Change the file extension from fluffy.jpg to fluffy.rar, then open and your file is there
b) Leave the file extension as is, right click, open with WinRar and your file is there
3D Desktop
Tired of your old desktop????
Here's a free software to convert your desktop into a 3D desktop. Here's a screenshot
A normal graphic card can also this application. So what are you waiting for, get this free software and convert your normal desktop into a 3D desktop.
Minimum system requirements
- Operating system Windows® XP / Vista
- Windows® DirectX 9.0c
- Intel® Pentium IV 1500 MHz
- 256 MB main memory
- DirectX capable graphic card: 64 MB NVIDIA® Geforce™ 3 or better,
ATI® Radeon™ 8500 or better - Screen resolution 800x600 at True Color (16 million colours)
- Internet connection
Day and Night on Your Desktop ! ! !

All in all its a very good tool, if you wish to see the earth from outer space and see how the day and night changes.
Download Desktopearth setup
Tuesday, October 21, 2008
How to run multiple yahoo messanger
- Select Start > Run
- Enter 'regedit' & click OK
- Goto 'HKEY_CURRENT_USER\Software\Yahoo\Pager\Test'
- Create a DWORD registry value named 'Plural' (without quotes) by right clicking on the right half of the Registry Editor window
- Double click the new DWORD entry and set the value to 1
- Its done!
Monday, October 20, 2008
Convert any image into a sketch
This would be the best software which you can use to make a cartoon of yourself or even your video. Before I really start talking about Hats off to the Bfunky Online Application which converts your images and videos into a perfect cartoon. Here is a sample of mine.
This online tool can do anything to make your image into a perfect cartoon and its pretty simple to use. Here are the following features which you would find in it:
- Cartoonizer
- Uvtar ( The image is the out come of uvtar)
- Video Cartoonizer.
 There are various levels, so you can select the amount of sketch or amount of cartoonising the pic according to your wish. Another good option is GOODIES. Here various tools are available to make the image look more appealing.
There are various levels, so you can select the amount of sketch or amount of cartoonising the pic according to your wish. Another good option is GOODIES. Here various tools are available to make the image look more appealing.You will be able to download the picture after you have Cartoonized it enough and you are happy about it. So what are you waiting for, rush man!
Using Gmail as a drive in windows
GMail Drive shell extension
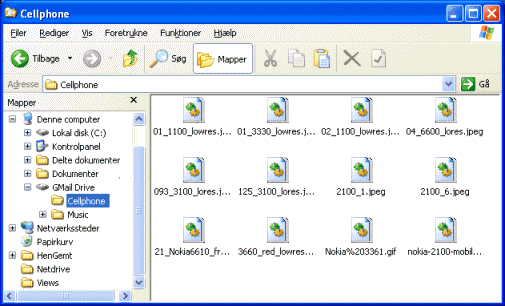
GMail Drive creates a virtual filesystem on top of your Google Gmail account and enables you to save and retrieve files stored on your Gmail account directly from inside Windows Explorer. GMail Drive literally adds a new drive to your computer under the My Computer folder, where you can create new folders, copy and drag'n'drop files to.
Ever since Google started to offer users a Gmail e-mail account, which includes storage space of 6000 megabytes, you have had plenty of storage space but not a lot to fill it up with. With GMail Drive you can easily copy files to your Google Mail Account and retrieve them again.
When you create a new file using GMail Drive, it generates an e-mail and posts it to your account. The e-mail appears in your normal Inbox folder, and the file is attached as an e-mail attachment. GMail Drive periodically checks your mail account (using the Gmail search function) to see if new files have arrived and to rebuild the directory structures. But basically GMail Drive acts as any other hard-drive installed on your computer.
You can copy files to and from the GMail Drive folder simply by using drag'n'drop like you're used to with the normal Explorer folders.
Because the Gmail files will clutter up your Inbox folder, you may wish to create a filter in Gmail to automatically move the files (prefixed with the GMAILFS letters in the subject) to your archived mail folder.
Please note that GMail Drive is still an experimental tool. There's still a number of limitations of the file-system (such as total filename size must be less than 65 characters). Since the tool hooks up with the free Gmail Service provided by Google, changes in the Gmail system may break the tool's ability to function. I cannot guarantee that files stored in this manner will be accessible in the future.
Installation Requirements
Internet Explorer 5 or betterInstallation Guide
- Extract the ZIP file to a temporary folder.
- Run the Setup application.
Download Files 
GMail Drive v1.0.13 - download site #1 (Softpedia)GMail Drive v1.0.13 - download site #2 (Betanews)
Save Disk Space
Disk Space is something how much you have is always less. New computers does come with hard disks which has boat load of disk space, but many people may have older computer where free disk space is not what it used to be. One option would be to upgrade or buy a new hard drive, but what if you're not that tech savvy.
Another option in Windows XP and Windows Vista is to compress the entire folder, so that every file that is stored on that folder is automatically compressed when saved and decompressed when opened. The beauty of this thing is that you don't need to compress or decompress the files, it is done automatically by Windows. You wouldn't even notice it. It's like working with any other normal folder.
Note: Before you try to compress a folder, make sure that folder is on NTFS file format.
Compressing the Folder to save Disk Space
- Right click the folder whose files you want to compress and click properties.
- Click on Advanced..
- Check the box which says "Compress contents to save disk space".
Speedy Shutdown in Windows
If you work on windows , you know that shutting it down can be really a hassle and time taking , especially when a lot of programs are running . Most of us tend to avoid shut down due to this reason but we know that shut down is always safer and also considered good for the pc .
There are a lot of shut down tricks and tools available , which help you to achieve a smooth and fast shut down of windows without negatively affecting your pc . However this trick , is probably the simplest one and also the fastest way to shut down your pc .
Here are the steps :-
1: Press Ctrl+Alt+Delete to go to the Task Manager .
2: Click on Shut Down on the Top .
3: Highlight ‘ Turn Off ‘ and while holding down the Ctrl key , click on it .
And thats it ! Just count 1 , 2 , 3…5 and there you go…your pc is off !
I have tried this trick on my XP system and it has worked everytime and hasn’t negatively affected my pc . I haven’t tried this on any other version of Windows but I think it’ll work .
However I advise you to use this trick only when you are in a rush and you need a speedy shut down of your pc .
Lock any folder in windows with out any software
Now follow the steps given below:
cls
@ECHO OFF
title Folder Locker
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}" goto UNLOCK
if NOT EXIST Locker goto MDLOCKER
:CONFIRM
echo Are you sure u want to Lock the folder(Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Locker "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}"
echo Folder locked
goto End
:UNLOCK
echo Enter password to Unlock folder
set/p "pass=>"if NOT %pass%==password here goto FAIL
attrib -h -s “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}”
ren “Control Panel.{21EC2020-3AEA-1069-A2DD-08002B30309D}” Locker
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Locker
echo Locker created successfully
goto End
:End
1.Copy above program into notepad.
2.The text which is written in bold letters delete it & type your password there.
3.Save that file by extension .bat ( name is Your choice)
4.Now on Your screen there is a bat file appear.
5.Double click on that file.
6.You will see the locker folder.
7.Save the files in that folder.
8.Double click on that folder & lock that folder
9.After locking that folder it will become hidden.
10.To open that folder double click on that bat file
11.Type your password & open that folder.
Thursday, October 16, 2008
Windows Vienna
Windows 7 (formerly codenamed Blackcomb and Vienna) is the next version of Microsoft Windows and the successor to Windows Vista Microsoft has stated that it is "scoping Windows 7 development to a three-year timeframe", and that "the specific release date will ultimately be determined by meeting the quality bar." Windows 7 will ship in both client and server versions with the client versions available in both 32-bit and 64-bit editions. The server version of Windows 7, Windows Server 2008 R2, is 64-bit only.
Although for a long period of time Microsoft maintained a "translucency" policy (rather than a "transparency" policy) in the lead up to the PDC, or Professional Developer's Conference, the Windows 7 project, features and technologies are slowly being revealed. Public presentations from company officials have disseminated information about some features and leaked information from people to whom the Milestone builds (M1, M2 and M3) of Windows 7 were provided also provides some insight into the feature set.
HISTORY
In 2000 Microsoft started the planning to follow up Windows XP and its server counterpart Windows Server 2003 (both codenamed Whistler) with a major new release of Windows that was codenamed Blackcomb (both codenames refer to the Whistler-Blackcomb resort). This new version was at that time scheduled for a 2005 release.
Major features were planned for Blackcomb, including an emphasis on searching and querying data and an advanced storage system named WinFS to enable such scenarios. In this context, a feature mentioned by Microsoft co-founder Bill Gates for Blackcomb was "a pervasive typing line that will recognize the sentence that [the user is] typing in."
Later, Blackcomb was delayed and an interim, minor release, codenamed "Longhorn", was announced for a 2003 release. By the middle of 2003, however, Longhorn had acquired some of the features originally intended for Blackcomb, including WinFS, the Desktop Window Manager, and new versions of system components built on the .NEt Framework. After the 2003 "Summer of Worms", where three major viruses − Blaster, Sobig, and Welchia − exploited flaws in Windows operating systems within a short time period, Microsoft changed its development priorities, putting some of Longhorn's major development work on hold in order to develop new service packs for Windows XP and Windows Server 2003 that included a number of new security and safety features. Development of Longhorn was also "reset" in September 2004 (see Mid-2004 to Mid-2005: Development "reset") as a result of concerns about the quality of code that was being introduced to the operating system. The eventual result of this was that WinFS, the Next Generation Secure Computing Base, and other features seen in some of the Longhorn builds were deemed "not ready" for wide release and as such did not appear in Longhorn when it was released as Windows Vista and Windows Server 2008.
As major feature work on Windows Vista wound down in early 2006, Blackcomb was renamed
Monday, September 22, 2008
Recreation of Big Bang (What gonna Happen)
Scientists have hailed a successful switch-on for an enormous experiment which will recreate the conditions a few moments after the Big Bang.
They have now fired two beams of particles called protons around the 27km-long tunnel which houses the Large Hadron Collider (LHC).
The £5bn machine on the Swiss-French border is designed to smash protons together with cataclysmic force.
Scientists hope it will shed light on fundamental questions in physics.
The first - clockwise - beam completed its first circuit of the underground tunnel at just before 0930 BST. The second - anti-clockwise - beam successfully circled the ring after 1400 BST.
 The LHC has been in construction for some 13 years |
On Thursday, engineers hoped to inject clockwise and anti-clockwise protons again, but this time they plan to "close the orbit", letting the beams run continuously for a few seconds each.
The BBC understands that low-energy collisions could happen in the next few days. This will allow engineers to calibrate instruments, but will not produce data of scientific interest.
"There it is," project leader Lyn Evans said when the beam completed its lap. There were cheers in the control room when engineers heard of the successful test.

He added later: "We had a very smooth start-up."
The LHC is arguably the most complicated and ambitious experiment ever built; the project has been hit by cost overruns, equipment trouble and construction problems. The switch-on itself is two years late.
The collider is operated by the European Organization for Nuclear Research - better known by its French acronym Cern.
The vast circular tunnel - or "ring" - which runs under the French-Swiss border contains more than 1,000 cylindrical magnets arranged end-to-end.
The magnets are there to steer the beam around this vast circuit.
Eventually, two proton beams will be steered in opposite directions around the LHC at close to the speed of light, completing about 11,000 laps each second.
At allotted points around the tunnel, the beams will cross paths, smashing together near four massive "detectors" that monitor the collisions for interesting events.
Scientists are hoping that new sub-atomic particles will emerge, revealing fundamental insights into the nature of the cosmos.
Major effort
"We will be able to see deeper into matter than ever before," said Dr Tara Shears, a particle physicist at the University of Liverpool.
"We will be looking at what the Universe was made of billionths of a second after the Big Bang. That is amazing, that really is fantastic."
The LHC should answer one very simple question: What is mass?
"We know the answer will be found at the LHC," said Jim Virdee, a particle physicist at Imperial College London.
The favoured model involves a particle called the Higgs boson - dubbed the "God Particle". According to the theory, particles acquire their mass through interactions with an all-pervading field carried by the Higgs.
The latest astronomical observations suggest ordinary matter - such as the galaxies, gas, stars and planets - makes up just 4% of the Universe.
The rest is dark matter (23%) and dark energy (73%). Physicists think the LHC could provide clues about the nature of this mysterious "stuff".
But Professor Virdee told BBC News: "Nature can surprise us... we have to be ready to detect anything it throws at us."
Full beam ahead
Engineers injected the first low-intensity proton beams into the LHC in August. But they did not go all the way around the ring.
Technicians had to be on the lookout for potential problems.
Steve Myers, head of the accelerator and beam department, said: "There are on the order of 2,000 magnetic circuits in the machine. This means there are 2,000 power supplies which generate the current which flows in the coils of the magnets."
If there was a fault with any of these, he said, it would have stopped the beams. They were also wary of obstacles in the beam pipe which could prevent the protons from completing their first circuit.

Mr Myers has experience of the latter problem. While working on the LHC's predecessor, a machine called the Large-Electron Positron Collider, engineers found two beer bottles wedged into the beam pipe - a deliberate, one-off act of sabotage.
The culprits - who were drinking a particular brand that advertising once claimed would "refresh the parts other beers cannot reach" - were never found.
In order to get both beams to circulate continuously, engineers will "close the orbit". The beams themselves are made up of several "packets" - each about a metre long - containing billions of protons.
The protons would disperse if left to their own devices, so engineers use electrical forces to "grab" them, keeping the particles tightly huddled in packets.
Once the beams are captured, the same system of electrical forces is used to give the particles an energetic kick, accelerating them to greater and greater speeds.
Long haul
The idea of the Large Hadron Collider emerged in the early 1980s. The project was eventually approved in 1996 at a cost of 2.6bn Swiss Francs, which amounts to about £1.3bn at present exchange rates.
However, Cern underestimated equipment and engineering costs when it set out its original budget, plunging the lab into a cash crisis.
Cern had to borrow hundreds of millions of euros in bank loans to get the LHC completed. The current price is nearly four times that originally envisaged.
During winter, the LHC will be shut down, allowing equipment to be fine-tuned for collisions at full energy.
"What's so exciting is that we haven't had a large new facility starting up for years," explained Dr Shears.
"Our experiments are so huge, so complex and so expensive that they don't come along very often. When they do, we get all the physics out of them that we can."
Engineers celebrated the success with champagne, but a certain brand of beer was not on the menu.
Sunday, September 7, 2008
How to remove Trojan downloader utility with all its sins
SmitFraudFix is a tool created to remove various desktop hijackers, adware and malware installed by Zlob family of trojans.
Operating System:
Windows 2000/XP
License:
Freeware
Download Here:
SmitFraudFix v2.250
Removal Procedure:
Important: Please print this procedure or download and print the PDF version as we have to close open windows during the process later.
1. Download SmitFraudFix by SiRi and save to your Desktop
![]()
2. Reboot your computer in SafeMode.
- Restart your computer
- Just before the computer begins to startup and before loading Windows press F8
- A selection menu should appear
- Select the line that says “Safe Mode”
- At logon prompt, log in as the usual user.
- During Windows Start process it will prompt you if you would like to continue running in SafeMode, press Yes
- You should now see your Desktop but in a low resolution mode only.
- Make sure no other application or windows is open.
3. Double-click on the Smitfraudfix.exe file which you downloaded earlier on your desktop. Press any key when the credit screen displays to proceed to removal procedure.
4. A selection menu will be displayed as shown in image below.
5. Press 2 on your keyboard, then Enter, to execute the selection - Clean (SafeMode Recommended)
6. It will begin to scan and clean your system thoroughly.
7. After that process, it will then run a Disk Cleanup tool to remove any unwanted files on your computer. It may take some time to complete this process.

8. After Disc Cleanup, it will show another prompt:

Do you want to clean the registry? (y/n). Press the Y button and then press the Enter to begin cleaning your registry.
9. This tool will also check if your wininet.dll is infected and will prompt:
Replace infected file? Press Y and then Enter to replace you wininet.dll with the clean version.
10. A reboot may be needed to complete the process. It will reboot your computer automatically, if not please restart your computer manually.
11. It will generate the report that can be found at the root of the system drive, usually at C:\rapport.txt. Keep this log file for your future reference.
Wednesday, September 3, 2008
Nokia Morph
By "Nanotechnology" they are able to transform 10,000 transistors on a single fly's hair.
So have a look....
Nokia and University of Cambridge launch the Morph - a nanotechnology concept device
February 25, 2008
New York, US and Espoo, Finland - Morph, a joint nanotechnology concept, developed by Nokia Research Center (NRC) and the University of Cambridge (UK) - was launched today alongside the "Design and the Elastic Mind" exhibition, on view from February 24 to May 12, 2008, at The Museum of Modern Art (MoMA) in New York. Morph features in both the exhibition catalog and on MoMA's official website.

Future shaping with Morph by Nokia
The Morph is mobile handset indeed, but there's more to it. It's a nanotechnology-driven concept device, which is on display at the New York Museum of Modern Art for a taster of the time when today's super gadgets will be museum exhibits of prehistoric knowledge.
The Morph is a concept that shows what nanotechnology can bring to mobile devices: flexible materials, transparent electronics and self-cleaning surfaces. Stretchable and foldable, transformable to any shape a user can think of, Morph is the ultimate transformers gadget changing its shape according to the user's wishes. One day you have a bracelet, the next - you are up with a QWERTY device for messaging.
With Morph the door is just ajar and it will be years before some of the innovations it explores will start to appear in actual high-end handsets
Tuesday, September 2, 2008
Backup of Bookmarks in Firefox
Bookmark Backup is a simple extension that helps to keep your bookmarks (and optionally other Firefox settings) safe. Each time Firefox is closed, a copy of your bookmarks file will be made to a backup location. If Firefox's bookmarks become corrupted or lost, find the most recent uncorrupted backup and copy it into your profile folder. By default the backups can be found in the Backups folder inside Firefox's profile folder, though this location can be changed in Bookmark Backup's Options dialog.
Note: Firefox 1.5 (and later) makes its own backup of your bookmarks.
- Close Firefox.
- Find the Backups folder in your profile folder (or in your custom backup location, if configured).
- Go into the sub-folder from yesterday (don't use today's backup, it will be corrupted). Copy whichever files you wish to restore into your profile folder.
- Restart Firefox.
If you have any problem with this and don't know how to perform any of these steps please feel free to e-mail me and I'll try to walk you through them.
Google trying to step a head

For those eager to download the beta version of Google's Chrome Web browser the best they can do for now is ponder the official screenshots of the browser. The availability of the beta Google Chrome browser is expected later today.
If the screenshots aren't enough for you there is also the Google Chrome comic book that explains what Google Chrome is and why it was developed.
As of this writing the Google comic book on Chrome appears to be overwhelmed and is not accessible. For an alternate browse of the Google Comic book check out this reprint at Google Books.
For background on Google Chrome check out earlier Today@PCWorld coverage.
Here are some of the screenshots taken from Google's official Google Chrome Web page (which appears to be inactive right now).

Here are the screenshots as they appeared on the Google Chrome site's front page. Note the site is not accessible right now with many speculating the official download will be available to the public at 2pm ET.

Screenshot shows Google Calendar and a pop-up window asking if you if you'd like to "Create shortcuts in the following locations." This seems to reinforce Google's drive to blur the line between Web-based applications and desktop applications.

Here is a close up of browser tabs utilized in Google Chrome. It appears that Chrome will create thumbnails of "most visited" Web sites visited and display them within a tab for easy access.

Google has spent a lot of time tackling memory issues related to its Chrome browser. Here is a screenshot that shows the Google Chrome Task Manager where you can manage processes running inside the browser such Java applications. Shutdown a browser "task" and Google Chrome will perform better.

This screenshot shows a feature called "Google incognito" that offers you the ability to browse the Net with a level of privacy and anonymity.

Google will incorporate an auto-complete function when typing in URLs directly into the browser. No word on whether this auto-completion feature will be related to "suggestion" feature added to Google search or something more similar to Firefox 3's Awesome Bar.

Bookmarking a website with Google Chrome appears to be identical to bookmarking a site with Firefox 3. Just click the star next the Web address and bingo it's saved. The real test will be how Google Chrome allows you to manage bookmarks.

Bookmarks along with other Chrome browser settings can be saved and retrieved in the Google cloud. This allows for anytime and anywhere access to your personal settings be it privacy, bookmarks, and history.

Far from its most exciting Google Chrome feature is this download status indicator. Google describes it as a way to "see your download's status at the bottom of your current window."
I like the way that Google rethinks common problems and issues (selling ads vs selling software, email, web browsing, etc) using current knowledge and high level goals to create new and simply elegant tools.
I remember when I first saw Gmail. My response was "that's it?", but then the simplified interface hid the power of it's new paradigm...exactly what new users need to make it easier to adopt.
Of course it's easy to introduce a completely new browser platform when you've got cash rolling in the way they do. Microsoft did the same thing when it had it's chance.
Michael Adams
www.chromevoice.com










