As I have discussed in my last post "How to block websites" now i am here with couple of solutions to unblock the blocked sites. So what are we waiting for? lets move to the solution.
The whole thing is happened due to most network administrators at work, university or school deny access to certain websites, instant messaging or social networks such as facebook, myspace or orkut with a firewall or proxy server. If you are constantly getting a message saying “Can’t connect” or something similar, the service you are trying to connect to have probably been blocked by your network administrator.
So, it’s time to focus on our main topic- how to bypass firewalls, proxy servers and hide IP address.
1: JAP (JONDO ANONYMITY & PRIVACY)Software Requirements
1-
JAP -> Download and Install.
2-
Java Runtime Enviroment(JRE) -> Download and Install.
There is an open source utility called JAP that protects our privacy on the Internet. In process to this it also helps to bypass firewalls and proxy servers.
Instead of connecting directly to a webserver, users take a detour, connecting with encryption through several intermediaries, so-called Mixes. JAP uses a predetermined sequence for the mixes. Such a sequence of linked mixes is called a Mix Cascade. Users can choose between different mix cascades.
Since many users use these intermediaries at the same time, the internet connection of any one single user is hidden among the connections of all the other users. No one, not anyone from outside, not any of the other users, not even the provider of the intermediary service can determine which connection belongs to which user.
Let’s learn how to configure it. Just follow the steps:-
1- After installation, open JAP and click on “Config” button.
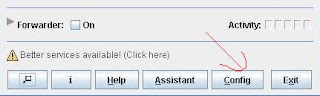
A “Settings” window will get opened.
2- Click on “Network” and if you are using any proxy to connect to the Internet then enter your proxy details under “Proxy/Firewall” section. Don’t forget to choose type of the proxy you are having.
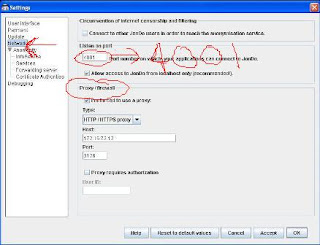
3- Next, choose “Services” under “Anonymity” option.
4- Click on the “Reload” button and after few minutes you’ll get a list of services called “Mix Cascades and single Mixes”
It is through these services we will get connected to the Internet, bypass the firewall and surf anonymously. It’s important to first understand these different types of services before start using it. There are basically 3 types of services that may be available to you at a given time. First one is the paid one, second is free services and third is the test service.
We will be focusing on Free Services here. Now how to recognize which service is of what type?
5- From the dropdown list above select “Mix cascades without costs“.
6- Now the RED stop mark before a service name shows it is “excluded by filter” which means it’s a paid service. But a BLUE ball mark before a service name shows it’s free to use.
7- Choose any one of the available free services and click on the “Select” button to activate it.
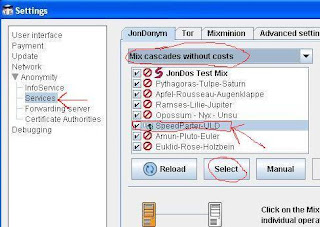
Free Services that I prefer are “Dresden-Dresden” or “SpeedParter-ULD”
8- Click “OK”.
That’s it. You are all set to connect to the Internet now.
9- Set Anonymity to “On“.
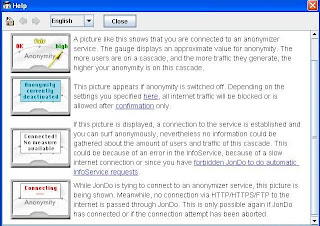
Soon JAP will get connected. Now, let’s learn how to use it.
To make web applications ( like Internet Explorer, YM, GTalk etc) work with JAP, use “IP address” 127.0.0.1 and “port number” 4001 under connection settings of your applications.
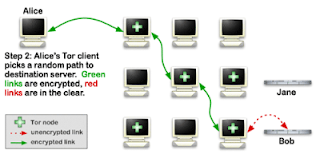
2: TOR (THE ONION ROUTER)Tor is a free application which is using for anonymous communication on the internet. Tor stands for The Onion Router. Tor Working with Onion routing technology. Onion routing is a technology for anonymous communication.
In this network all the users will work as a router. when you send a request to a server the Tor will encrypt the packet with many layers. Each Onion Routers removes a layer of encryption and send to another Onion Router. Tor also protect its users against traffic analysis attacks
So you can use Tor as a Anonymous Proxy, You can bypass firewall / proxy with Tor. Surf restricted sites with Tor. Go to
www.torproject.org for more details.
If you are a proxy user you have to give the details in setting tab
 Download Tor3: ULTRA SURF
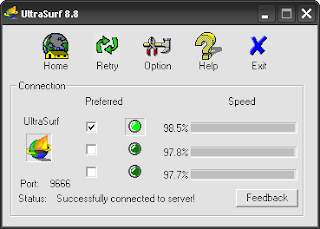
Download Tor3: ULTRA SURFUltraSurf is a proxy application. It will Bypass All Internet Blocking Systems. By using this software you can access all the sites blocked by national / corporate firewalls. It is a free application. It brake all the access list. This application is nothing but just searching the proxy list which is fast and available. It will automatically change our IE’s proxy server to local proxy. That means this application will work as a web proxy server. Most of the schools and co-operates are blocking dating sites like orkut , myspace. And some sites like YouTube ( for bandwidth ). Most of them depending web proxys to bypass them. But they won’t get the full feeling of a normal browsing , because the sites are with banners.
It is a small EXE. There is no need to install the application. Just run in ..
Features
1, 100% freedom to have 100% information in most secure way.
2, It means no matter where you are you can access 100% of internet I mean no firewalls no restriction nothing….
3. Almost all schools, universities and corporate offices raise firewalls to filter out not work related sites, now those firewalls will be of no use or they have to change their plans.
4. Everybody can access various social networks like Orkut, Youtube, Myspace, Hi5, Facebook, Linkedin etc. which are blocked almost in 99% schools and offices.
5. 100% real time and it’s encryption is better then any online banking system.
If you are using browsers other than IE, You have to manually change the proxy settings .
Proxy settings as follows..
HTTP Proxy : 127.0.0.1 Port : 9666
Download Links:-
http://www.wujie.net/downloads/ultrasurf/u.zip
http://www.ultrareach.com/company/download.htm
http://rapidshare.com/files/71216473/U88.exe
http://www.box.net/shared/9im3yq3bg9